Innovative digital identity company in the
Middle East and Africa.
Onboard new users faster, easier, and cheaper with an experience that seamlessly fits into your onboarding journey. Fully supported across the Middle East & Africa.
Our digital identity partners
Explore the most cutting-edge digital identity tech stack in MEA
Award-winning, fast and seamless digital identity verification process
Step 1
Read the document and extract identity data.
Step 2
Check the person on camera is real and matches the document.
Step 3
Verify the individual via government databases.
Step 4
Check customers are worthy of doing business with AML & sanctions screening.
Step 5
Enable passwordless login and strengthen authentication with biometrics.
Pushing boundaries in the identity space in MEA and beyond
Licenses sold
EMEA Document Scanning Coverage
Global Passport NFC Reading
Awards & Recognitions
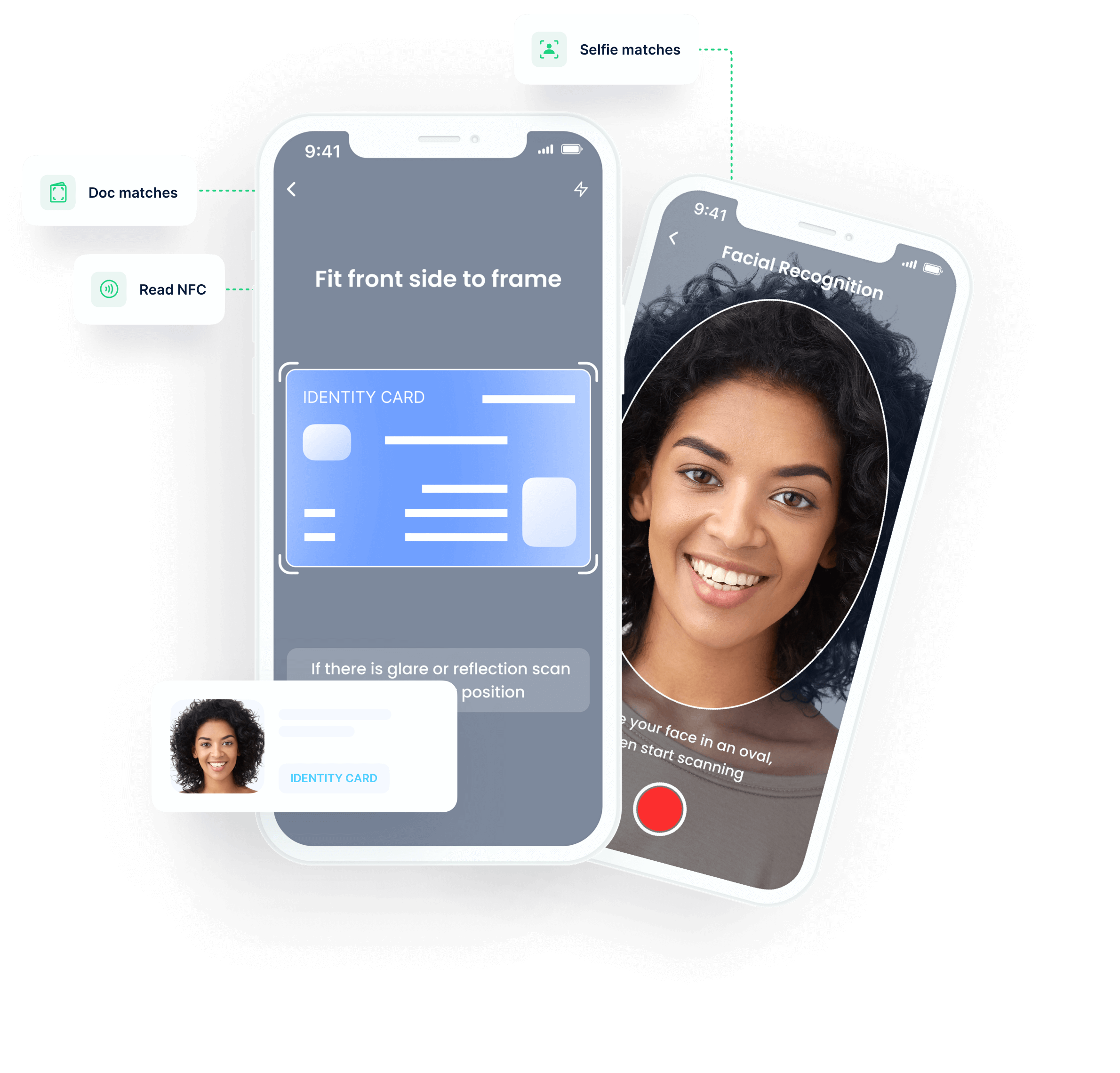
Digital KYC+ verification services
Increase conversion rates by providing faster access to your services, reduce costs by eliminating manual checks, and minimise risk with our best-in-class digital onboarding solution:
-
KYC
- Market-leading AI document scanning
- Unmatched NFC reading capability
- Face verification in under 3 seconds
- Document verification via public & private databases
-
Enhanced due diligence
- Bank account verification
- Duplicate detection
- Address verification
- Credit check
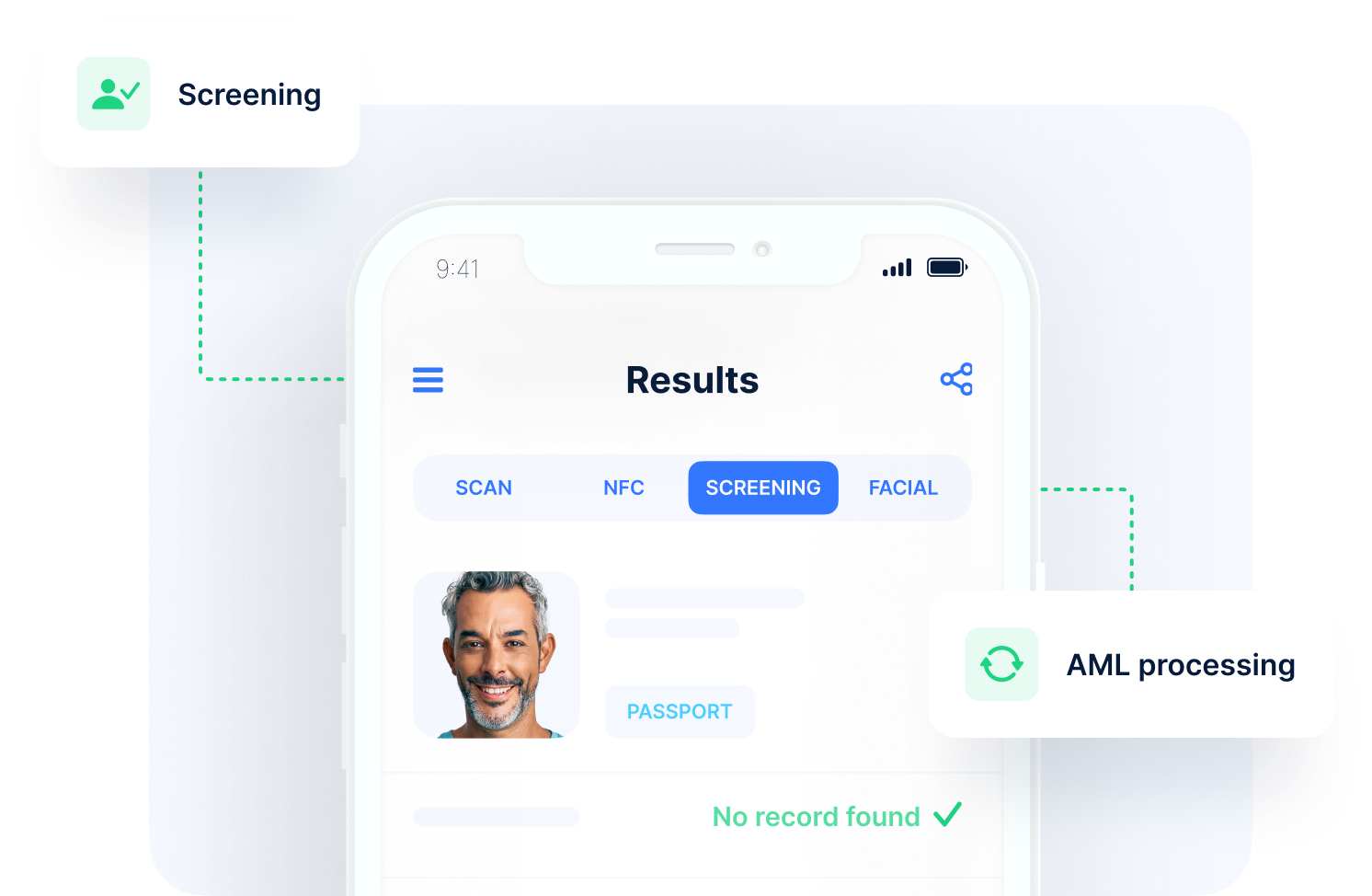
Screening: AML & sanctions solutions
Full-stack screening from the world’s largest global risk database with checks across Monitored Lists, PEPs, and Adverse Media.
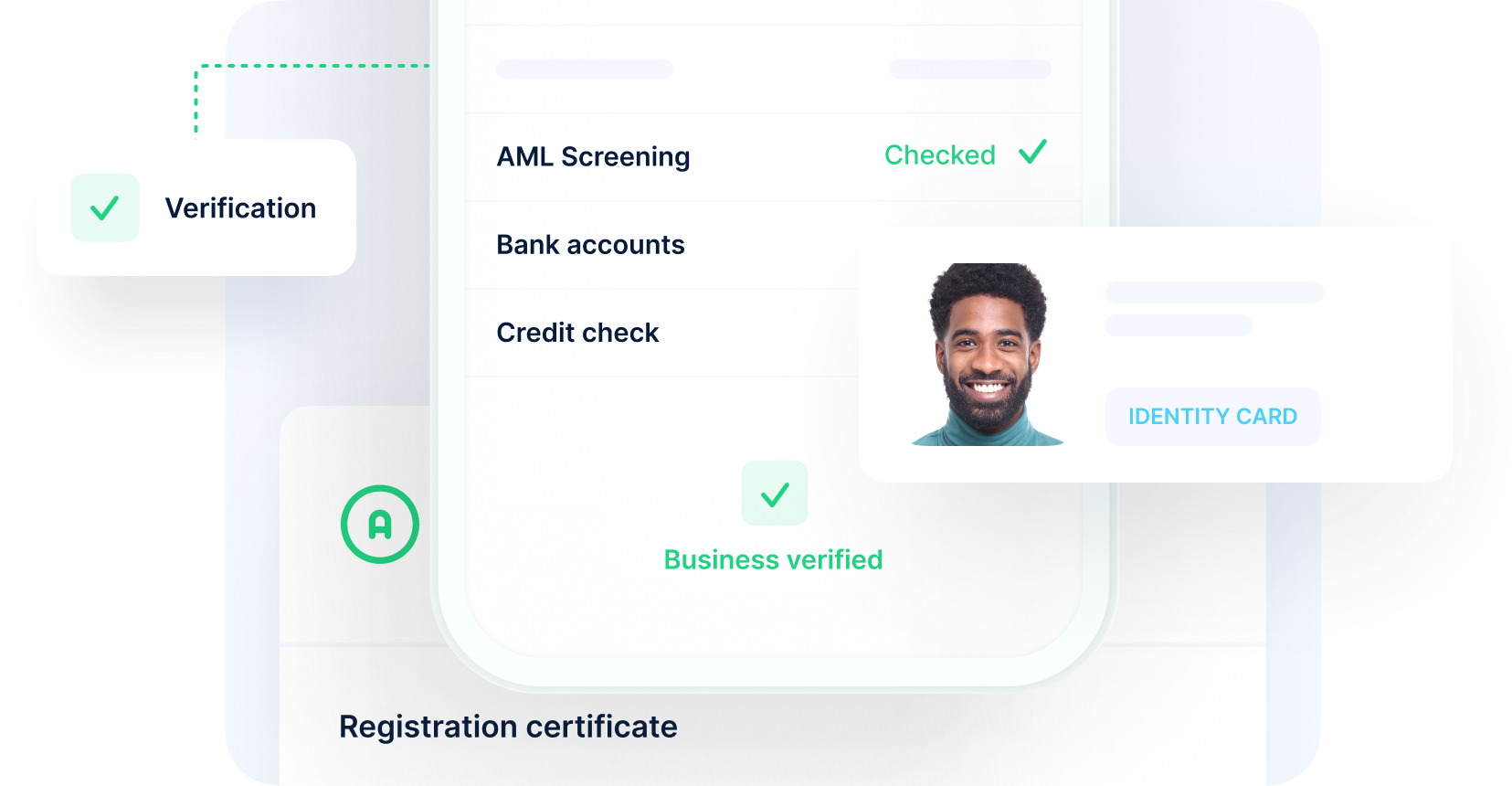
Know your business (KYB) solutions
Screen from the world’s largest individual and company lists to verify business authenticity. Identify Ultimate Beneficial Owners, run AML screening, verify bank accounts, check credit, and much more.

Legitimate and safe authentication services
Leverage state-of-the-art biometrics
for passwordless login, multi-factor authentication, account recovery, transaction authorisation and more.
An award-winning team
uqudo is proud to be recognised by some of the world’s most distinguished organisations.
Secure, frictionless, & fully compliant digital onboarding. Integrated seamlessly within your app.

Our clients
Easily integrate  with your tech stack.
with your tech stack.
Use our simple and secure Web SDK, Mobile SDK, or RESTful API to seamlessly integrate identity capabilities into your operations.
See documentationPress & Media
The relationship between Digital National Identity programs and Economic Growth in Africa & Emerging Markets
uqudo Greenhouse Capital

Stay up-to-date with the world of identity.
Subscribe to get the latest identity artcles, guides and videos, straight to your email.
We’re committed to your privacy uqudo uses the information you provide to contact you about our content, products, and services. You may unsubscribe from these at any time. For more information, check out our privacy policy.












































 with your tech stack.
with your tech stack.